An Intrusion Detection System (IDS) is a software that monitors networks or systems for malicious activity. In this article we will be seeing how you can setup an IDS for your WordPress website.
Suspicious activity is typically a sign that someone is trying to find a security hole on your WordPress website. Sometimes, it is also a sign that your website have already been hacked.
Why do you need a WordPress Intrusion Detection System?
The earlier you notice a hack attempt the sooner you can thwart the attack from happening, thus ensuring your website incurs no damages.
In a post-hack attack, it is also important to identify the hack at the earliest possible. The earlier you identify a hack attack the more you can limit the damage and the easier it is to recover your WordPress website.
This article explains how to build an Intrusion Detection System for your WordPress websites with the WP Activity Log plugin, the most comprehensive activity log solution for WordPress.
Detecting & getting notified of WordPress hack attempts
Prevention is better than cure. So let’s start with the prevention first. What do malicious hackers typically do to find vulnerabilities and security weaknesses on your WordPress websites? They use automated software and scripts to:
- scan your website and detect possible old and vulnerable plugins, themes or WordPress core,
- brute force attack your WordPress website to try to guess weak credentials (hence why it is important to enforce strong password policies),
- identify insecure WordPress defaults that could give them some leverage against your website,
- find security weaknesses that could give them information to help them launch more sophisticated attack, such as developers leftover files, database exports and disclosure of sensitive information.
The above activity is very easy to detect. Automated tools that scan websites create a lot of noise, so you can create notification rules in WP Activity Log to get alerted via email or SMS when your website is scanned or is a target of a brute force attack. Here is how;
Detecting Automated WordPress Security Scans
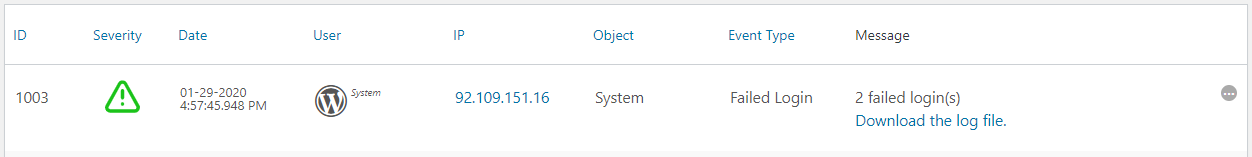
An automated scanner sends thousands of HTTP requests, trying to exploit known vulnerabilities in WordPress, a plugin or a theme. This activity generates a lot of HTTP 404 errors. The WP Activity Log plugin keeps track of all requests to non-existing pages with two event IDs:
- Event ID 6007 for 404 errors generated by logged in users,
- Event ID 6023 for 404 errors generated by anonymous users.
An automated scan is unauthenticated, so we are looking for event ID 6023. Using the below screenshot as an example, you can easily identify automated scans in the WordPress activity log.
Note: it is normal to see a few event ID 6023 on a daily basis. It becomes a problem when you see thousands of requests in a short span of time.
The plugin can also log all the HTTP 404 errors to a log file. Analyze these log files to learn about the type of attacks or vulnerabilities attackers are trying to find on your WordPress website.
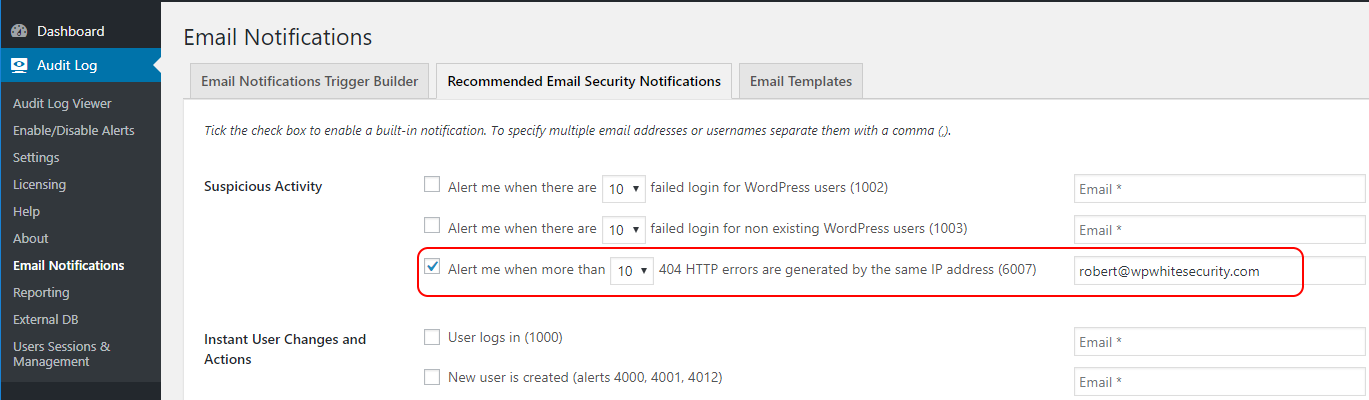
Get instantly notified when your WordPress is scanned for vulnerabilities
To receive an email or SMS notification when your website is being automatically scanned, enable the 404 HTTP errors alert from the Recommended Email Security Notifications tab in the Email Notifications menu node.
Detecting WordPress login page brute force attacks
During a WordPress brute force attack, attackers try to guess WordPress usernames and passwords using automated software. Typically, attackers use a dictionary of commonly used usernames and passwords during the attack. Below are some examples of commonly user username and password combinations:
- admin/admin
- admin/password
- admin/qwerty
- admin/administrator
- administrator/administrator
- administrator/password
- administrator/qwerty
- administrator/12345678
WordPress Security Tip: always enforce strong WordPress password policies so attackers cannot guess your or your users’ credentials.
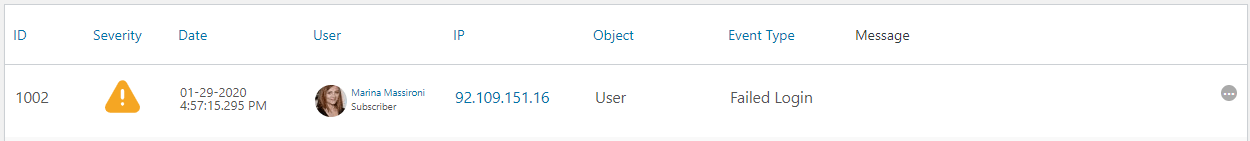
For every username and password combination the software tries, there is a failed log in on your WordPress website. The WP Activity Log plugin keeps a log of failed logins with the following event IDs:
- 1003 for a log in with a non-existing user,
- 1002 for a user failed log in.
Get instantly notified of a WordPress brute force attack
Similar to what we have done to for automated scans, configure the plugin to instantly alert you via email or SMS when there are failed login attempts on your WordPress. As per the screenshot below, you can enable either one of the rules, or both.
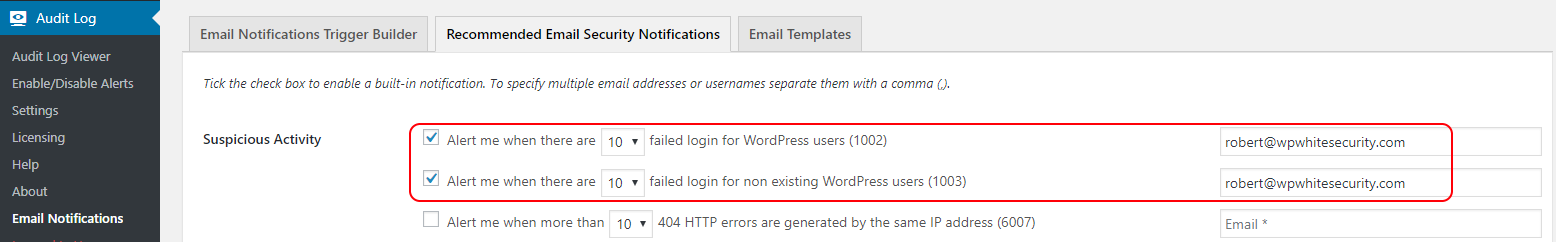
I’d recommend you to not bother with failed log in attempts of non-existing usernames. However, keep an eye on failed log in attempts using existing usernames, as explained in Dealing with Failed WordPress Logins.
Detecting successful WordPress hacks
There is no bullet-proof WordPress security solution. You can have the best WordPress firewall, malicious hackers might still find a way in. Therefore it is imperative to getting notified should the worse happen; when your WordPress is hacked. The earlier you find out about a hack, the easier the recovery process is.
First things first; to configure a good IDS you need to understand what hackers typically do when they hack a WordPress website. For example they:
- Create a new username and use it to retain backdoor access,
- Install their own plugins,
- Modify content, widgets etc,
- inject malicious code in the source code files.
Let’s see how you an use the email and SMS notifications in WP Activity Log to get instantly alerted of any of the above changes. This will allow us to catch hackers red handed and limit the damage.
Get notified when a hacker creates a new WordPress user & logs in with it
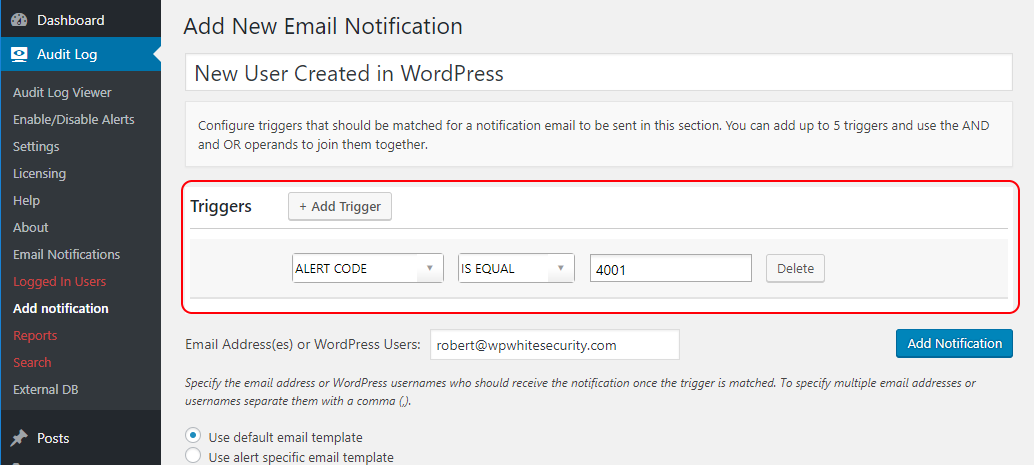
The WP Activity Log plugin uses event ID 4001 to keep a log when a new user is created on WordPress. So by creating the below trigger you will be alerted via email and / or SMS when a new user is created on your website:
EVENT ID IS EQUAL 4001
Get notified of a new user log in
Depending on the vulnerability attackers manage to exploit, or the access they gain, they can also create a new WordPress user directly in the database. However, the WP Activity Log plugin can still alert you of such activity by enabling the Alert me the first time a user logs in notification. Below is a screenshot of an email notification, alerting the WordPress administrator that a user logged in to the WordPress website for the first time.
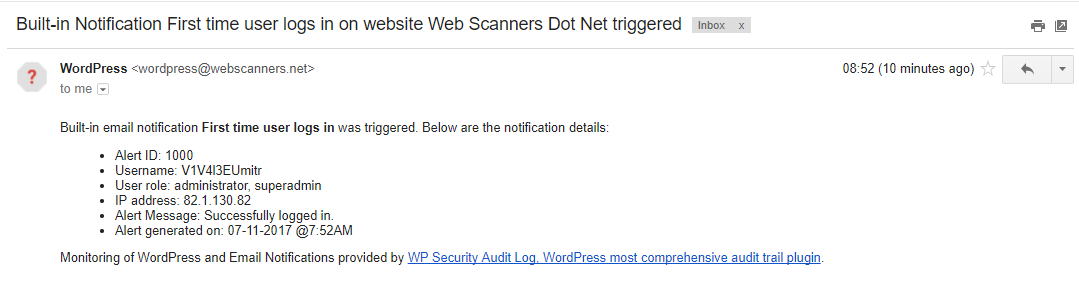
Get notified of suspicious log in activity on your WordPress
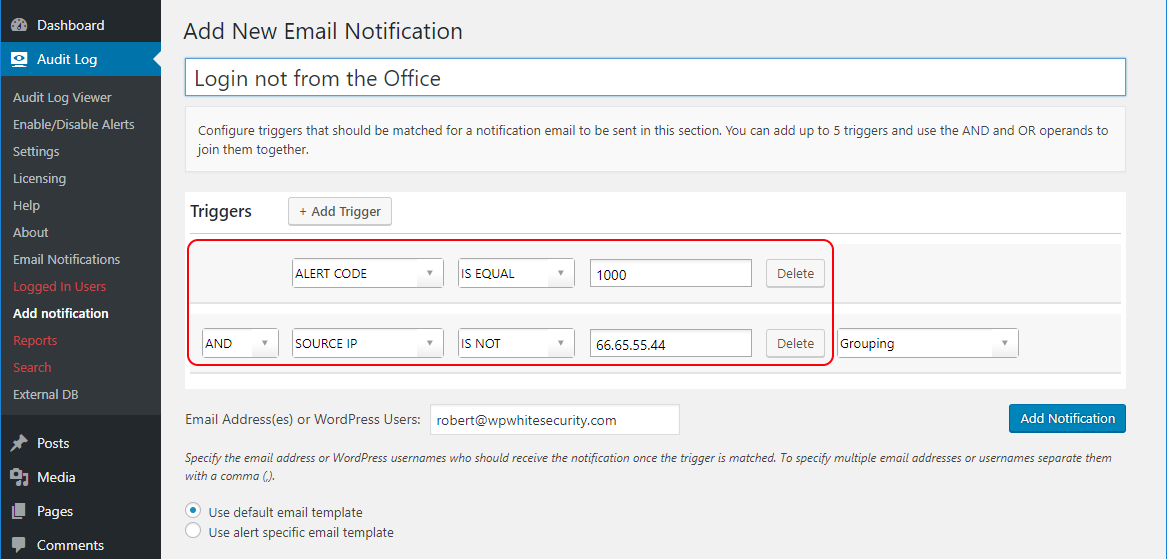
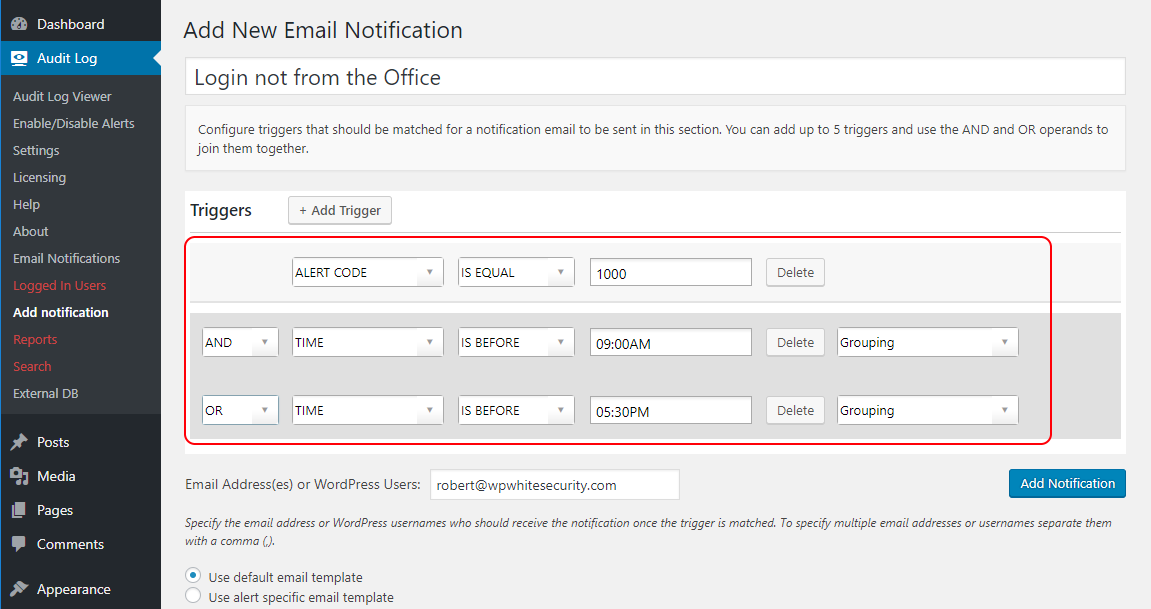
With the Notifications feature in the WP Activity Log plugin you can build more complex notifications rules by using the AND and OR operands, and groups. For example, if your team always log in to WordPress from the office, which has a fixed IP address of 66.65.55.44, you can create a notification to send you an email and / or SMS when there is a login that is not from the office’s IP address. Following is the example rule:
ALERT ID IS EQUAL 1000 AND IP ADDRESS IS NOT EQUAL 66.65.55.44
You can also create a notification to be alerted when someone logs in outside office hours. For example the below trigger will send an email or SMS message when someone logs in to WordPress outside the office hours (9AM – 5:30PM):
Alert ID Is Equal 1000 AND (TIME is before 9am OR TIME is after 5:30pm)
Notice the brackets. They are used to group criteria. Use the grouping drop down menu next to every criterion to configure them:
Get notified of other suspicious WordPress user activities
Use the Email and SMS Notifications in WP Activity Log to be alerted of any possible change that happens on your WordPress. The options are endless because the plugin keeps a log of all these changes that happen on your WordPress website. From a security point of view, I recommend configuring a notification for when a user:
- changes the password of another user,
- logs in from a different IP address (if user always logs in from the same IP address),
- logs in during odd hours,
- installs or activats a plugin.
Browse through the list of changes that the plugin can keep a record of for more ideas on what type of email and SMS notifications you can configure to be alerted of possible suspicious activity.
It’s simple! Configure your own WordPress Intrusion Detection System
By understanding how your WordPress website is used and how your team operates, you will be able to configure a solid WordPress Intrusion Detection System that helps you prevent possible attacks and save you on a rainy day.
Last but not least, take all the other necessary security precautions. After all, WordPress security is a continuous process and not a one time fix!