Search for answers or browse our knowledge base.
WP Activity Log Support for Reverse Proxies & Web Application Firewalls
WP Activity Log automatically retrieves the originating IP address of a user even when WordPress is running behind a reverse proxy, a web application firewall or load balancers.
WP Activity Log WordPress plugin can be configured to retrieve the originating IP Address of a WordPress user even if WordPress is running behind a reverse proxy, web application firewall or load balancers. This article explains how WP Activity Log can retrieve the originating WordPress user’s IP Address and not that of the proxy, firewall or load balancer.
WordPress and Reverse Proxy or Firewall Setup
In a typical setup, the reverse proxy or web application firewall is installed in front of the WordPress server. Therefore the user never communicates directly with WordPress. The user communicates with the reverse proxy and the proxy communications with WordPress, as seen in the below screenshot.

Hence in such a setup the default installation of WP Activity Log sees all the requests originating from the reverse proxy, which is 192.168.2.15. In such case all events in the activity log will have 192.168.2.15 as originating IP address. To record the originating WordPress user IP address enable the option in the Reverse Proxy / Firewall Options as explained below.
Recording the originating IP Address in the WordPress activity log
WP Activity Log plugin has two options related to reverse proxy, firewall or load balancers WordPress setups, as seen in the below screenshot. You can toggle the status of these settings from the General tab in the plugin settings.
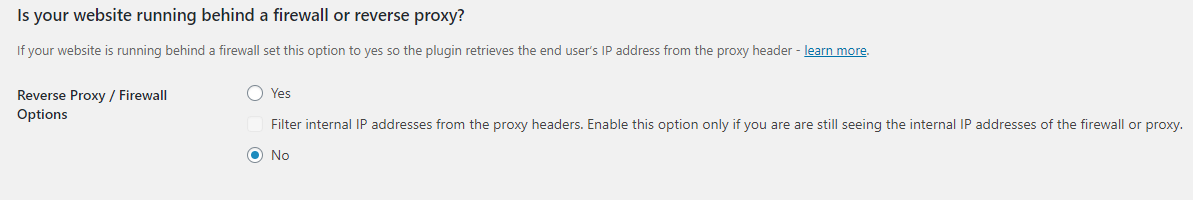
WordPress Running Behind Firewall or Proxy Plugin Setting
When the first option WordPress running behind firewall or proxy is enabled, the plugin will retrieve the users’ IP address from any of the below headers, thus reporting the IP address of the user and not that of the firewall or proxy:
- HTTP_CLIENT_IP
- HTTP_X_FORWARDED_FOR
- HTTP_X_ORIGINAL_FORWARDED_FOR
- HTTP_X_FORWARDED
- HTTP_X_CLUSTER_CLIENT_IP
- HTTP_FORWARDED_FOR
- HTTP_FORWARDED
- REMOTE_ADDR
- HTTP_CF-Connecting-IP (used by Cloudflare)
- HTTP_TRUE_CLIENT_IP (used by Cloudflare)
All of these headers are used by proxy servers, firewalls and load balancers to identify the originating IP address of a client connecting to a web server through a proxy, web application firewall or load balancer. The below screenshot shows the headers of connection being forwarded via a reverse proxy:
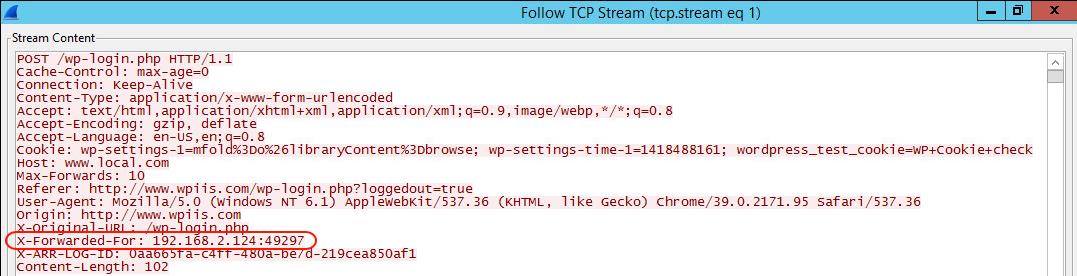
In some cases the connection between a WordPress user and a WordPress website can be routed through several network hops and such header can contain multiple IP addresses. WP Activity Log always reports the first IP address from the left as the originating one, as instructed in the RFC standards. Though it still stores all IP addresses in the headers as explained in the section below Retrieving All IP Addresses Reported in HTTP Headers.
Filter Internal IP Addresses Plugin Setting
By enabling the option Filter Internal IP Addresses, WP Activity Log plugin will not report the end user IP address should it be an internal IP address. This option has been implemented because in some cases there is the possibility that an internal IP is reported in the HTTP headers rather than a public IP address.
Retrieving All IP Addresses Reported in HTTP Headers
WP Activity Log plugin records all the IP addresses specified in any of the HTTP headers mentioned above but only displays the first one from the left since that should be the WordPress user originating IP address as per the RFCs. Though there might be cases where some servers do not follow the RFC and change the order of the IP addresses in these HTTP headers. In such situation, should you wish to see all the IP addresses reported in the HTTP headers follow the below procedure:
- Enable the option Data Inspector from the Developer Options in the plugin’s settings
- Click on the more details icon (…) of that alert for which you would like to see all the data
- Expand the Other IPs node to see all other IP addresses specified in the header as shown in the screenshot below.

From the above screenshot you can notice that the reverse proxy used the HTTP_X_FORWARDED_FOR header and the WordPress user’s originating IP address is 192.168.2.124. You can also notice the proxy’s IP address 192.168.2.15 in the REMOTE_ADDR header.
